An Apple patent (number 20120281828) for the protection of audio or video in a playback device has appeared at the U.S. Patent & Trademark Office. It involves a method and apparatus to prevent hacking of encrypted audio or video content during playback.
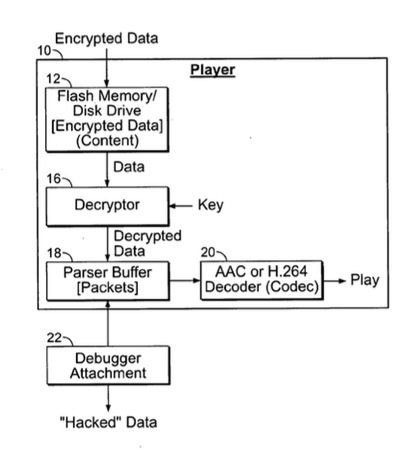
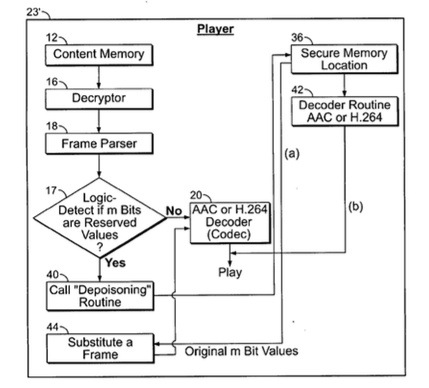
Hackers, using a debugging attachment or other tools, can illicitly access encrypted data in memory in a playback device when the data is decrypted during playback and momentarily stored in digital form. This hacking is defeated here by methodically "poisoning" the encrypted data so that it is no longer playable by a standard decoder.
The poisoning involves deliberate alteration of certain bit values. On playback, the player invokes a special secure routine that provides correction of the poisoned bit values, for successful playback.
Here's Apple's background on the invention: "The protection of digital content transferred between computers over a network and transferred from a computer to an associated playback device is important for many organizations. The DRM process often involves encrypting the pieces of content (e.g., encr the binary form of the content) to restrict usage to those who have been granted a right to the content, which is typically pieces of music or video programs.
"Cryptography is the traditional protection method, but for many digital file transfer situations, a party that legitimately receives the content might try to break the DRM protection scheme, so as to give illicit access to third parties. An identified weak leak in the DRM security is in the overall process, rather than the encryption scheme. For instance, one of the more successful DRM systems distributes music and video content via the Internet.
"The DRM system distributes to a user's computer content that has been encrypted. The user's computer then decrypts the received content, generates local keys for encrypting the content, and uses these local keys to re-encrypt the content. Typically the content in encrypted form may also be downloaded, via a local connection, to an associated playback-only device such as an audio or video media player, which similarly decrypts and re-encrypts the content before playing same.
"The present inventors have identified a potential security issue with this approach. As indicated above, during the playback process (which can also occur in the user's computer) the decrypted data is resident for a time in memory in the host computer and/or other playback device. One such memory location is a buffer memory which temporarily stores one or more packets or frames of the decrypted content bitstream. For audio content, the usual encoded format of the data is referred to as AAC (Advanced Audio Coding ISO 13818-7) which is a compression standard with associated codecs (coder-decoder) commercially available in hardware and software. For video, the usual encoded format is H.264, a similar standard with compression, also with commercially available codecs.
"During the playback process, portions of the decrypted content (packets for audio, frames for video), are temporarily stored in a buffer prior to being supplied to the AAC or H.264 or other decoder. Hackers (illicit copiers) may be able to access the decrypted data in this buffer using a standard software tool known as a debugger attachment. The hacker can then copy the accessed data out of the buffer, store it, and as the content is played thereby have a decrypted copy of the entire content, without having to break the actual encryption."
The inventors are Julien Lerouge, Gianpaolo Fasoli and Augustin J. Farrugia.